Introduction
If you planning to require Entra/AAD group membership to view content, then please ensure that WPO365 is able to retrieve a list of Entra/AAD groups that a user belongs to. WPO365 will use that information to assign users to an Audience; A virtual group of users that is dynamically populated with members of one or more Azure AD groups. A user’s assignment to one or more audiences is re-evaluated each time a user signs in and each time the user is updated through WPO365’s user synchronization processor.
User login
When a user signs in with Microsoft, WPO365 receives either an ID token – when OpenID Connect based SSO is configured – or a SAML 2.0 response – when SAML 2.0 based SSO is configured. Both responses can be configured, to include a list of the Entra/AAD groups that a user belongs to.
ID token
Perform the following steps to include a list of Entra/AAD groups that a user belongs to in the ID token.
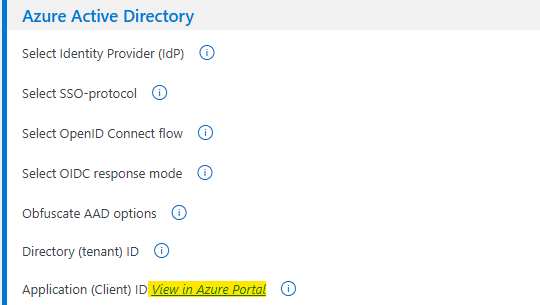
- Go to the plugin’s Single Sign-on configuration page.
- Click the View in Azure Portal link for the Application (Client) ID setting, to open the configuration pages for your registered application in Azure Portal.
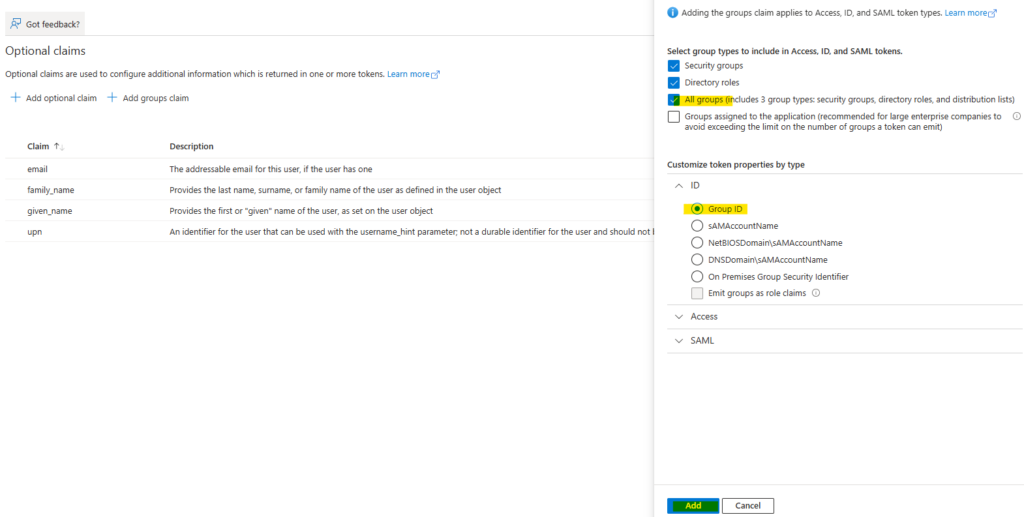
- Expand the Manage section and click Token configuration.
- Click + Add groups claim, select All groups, ensure that for the ID (token) the Group ID is selected and confirm your choice by clicking Add.
SAML response
Perform the following steps to include a list of Entra/AAD groups that a user belongs to in the SAML 2.0 response.
- Locate the Enterprise Application that you created previously when you registered the WordPress application in Entra/AAD by navigating to Entra Portal > Identity > Applications > Enterprise Applications.
- Click the entry in the list of Enterprise Applications to open its configuration pages and continue to the Single sign-on page.
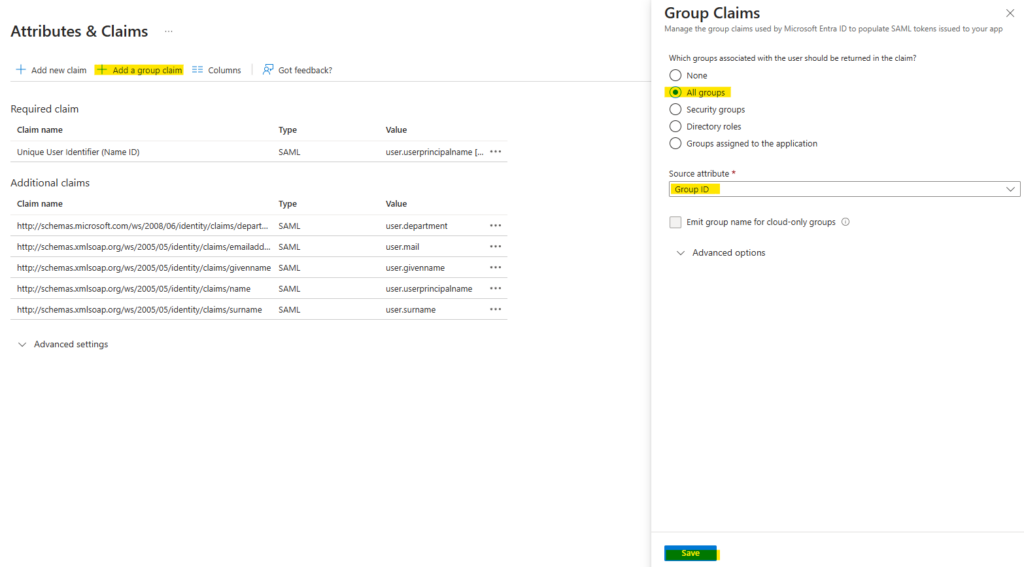
- Edit the list of Claims & Attributes, as shown below.
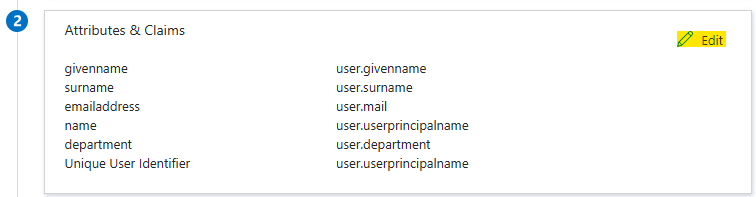
- Click + Add a group claim, select All groups and ensure that the Source attribute is Group ID, before clicking Save.

The number of Entra / AAD Group IDs that an ID token and SAML 2.0 response can contain is limited to around 200. If a user is a member of more groups than the limitation allows, the response won’t contain the list of Group IDs and WPO365 may not work as expected. To work around this, WPO365 is able to retrieve the list of Group IDs from Microsoft Graph instead. To configure, you must first ensure that the ID token or SAML 2.0 response does not include the groups claim. Instead, you must make sure that WPO365 has application-level access to Microsoft Graph, as explained in the paragraph “User synchronization”.
User synchronization
Perform the following steps to enable WPO365 to retrieve a list of Entra/AAD groups that a user belongs to, from Microsoft Graph when it synchronizes users and their attributes.
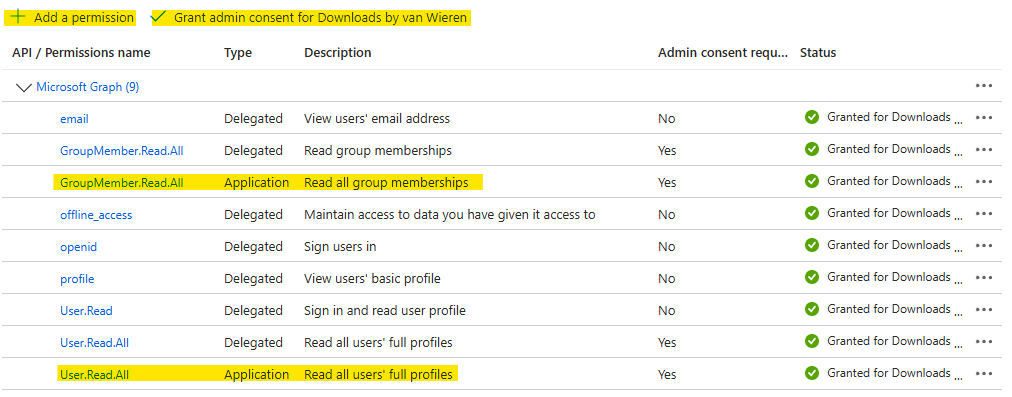
- Make sure to click Grant admin consent for [your tenant name]. If that link is greyed out, then ask your Entra Global Administrator to click that link for you.
- Switch to your WordPress backend / admin area and continue to WPO365 > Integration configuration and check Use app-only token and (recommended when you configured OpenID Connect based SSO) Use existing App registration From the Single Sign-on tab.
- Ensure to save the updated WPO365 configuration.

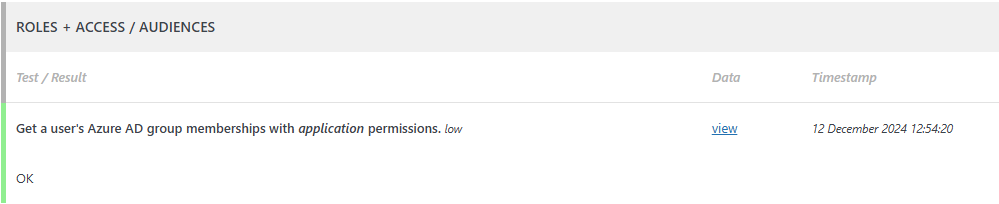
Testing the retrieval of Entra / AAD groups for a user
Perform the following steps to test the retrieval of Entra / AAD groups for a user.
- Go to WP Admin > WPO365 > Plugin self-test.
- Click Start self-test.
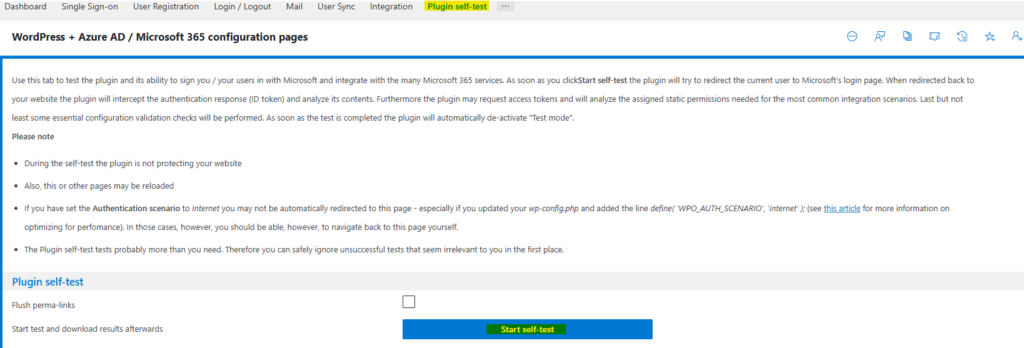
- Authenticate using your Entra / AAD account when asked to do.
- Once the self-test finished, you should have been automatically redirected back to Plugin self-test page and you’ll find the test result when scrolling down, for example whether or not the SAML response contained a “groups” claim and whether or not WPO365 can successfully request a list of Entra / AAD groups that a user is a member of from Microsoft Graph.